Problem Statement
Cloud environments are becoming increasingly complex and distributed. Auditing user activity, service behavior, API calls, or identifying anomalous actions in AWS is almost impossible to perform manually.
CloudTrail records every event, but the challenges are clear:
- Inability to quickly investigate incidents
- Missing unusual activity patterns
- Lack of clear user-behavior visualization over time
- No tool to answer natural-language audit questions like:
- Who accessed IAM last week?
- List failed console logins by region
This is where an AI-powered cloud auditing solution becomes essential.
Solution
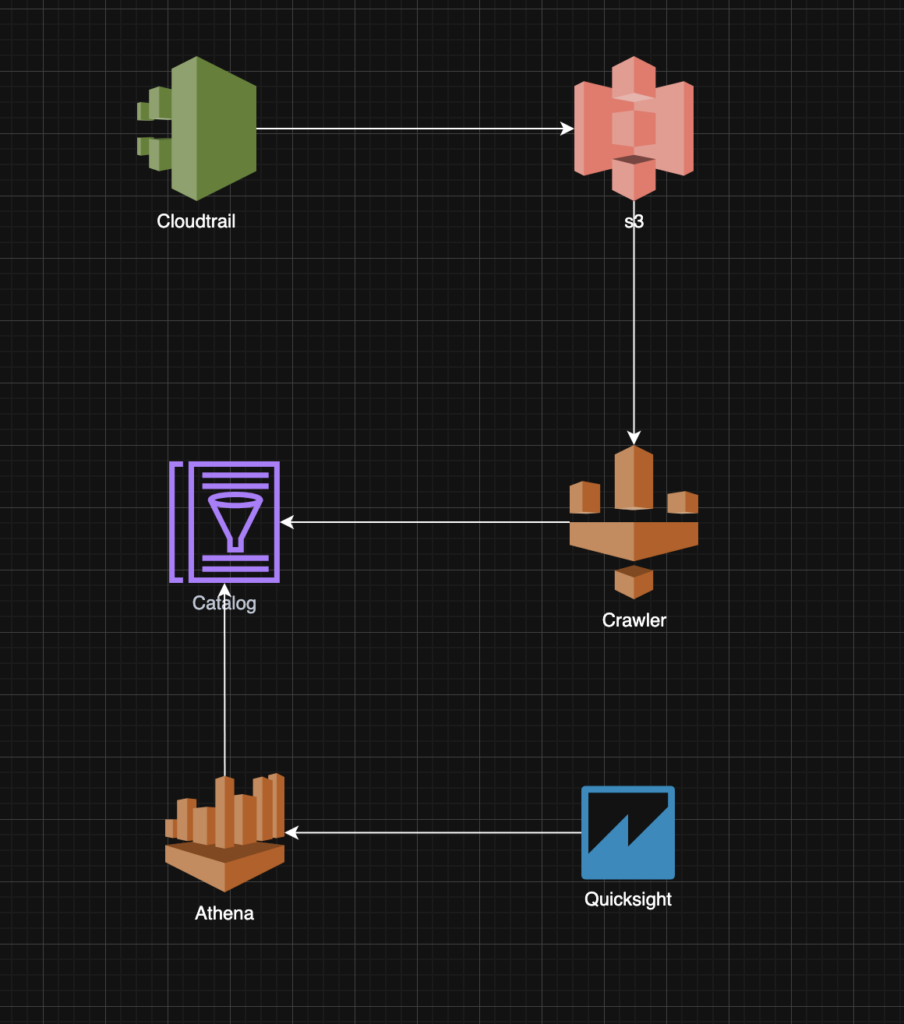
Key notes of this solution
- Leverage Amazon Q’s AI capabilities to perform natural-language queries on CloudTrail data
- Quickly identify unusual or risky activities without writing SQL
- Instant visualization of audit findings through QuickSight + Q
This solution is intentionally simple. You ingest CloudTrail logs into Amazon S3, use an AWS Glue Crawler to periodically catalog the data, and query it using Amazon Athena.
Athena then becomes the primary data source for visualization and AI-driven querying.
By connecting the Athena dataset to QuickSight Q, Amazon Q automatically learns from the ingested CloudTrail dataset. It can then answer high-value audit questions such as:
“Which actions did user X perform during time window Y, and how do those actions differ from their typical daily behavior?”
The biggest challenge in cloud auditing is not the lack of data, it’s the overwhelming abundance of it.
CloudTrail captures every API call, every user action, and every system event.
But without an effective way to extract meaningful insights, this massive data stream becomes practically unusable.
This solution bridges that gap by combining:
- the analytical power of Athena for large-scale log querying
- the intelligence of Amazon Q, enabling natural-language questions and AI-driven insights
Together, they transform raw CloudTrail logs into actionable audit intelligence, making it faster and easier to detect anomalies, investigate unusual user behavior, and visualize risk patterns in real time.